
Man-in-the-Middle (MitM) attacks pose a serious cybersecurity threat by intercepting and manipulating communication between users and applications to steal sensitive information. These attacks exploit vulnerabilities in communication protocols and user behaviors, making them a common method for identity theft and unauthorized transactions. Understanding how MitM attacks work and implementing effective preventative measures is crucial to protect against these threats. This overview covers the mechanisms of MitM attacks, common types, and strategies for prevention.
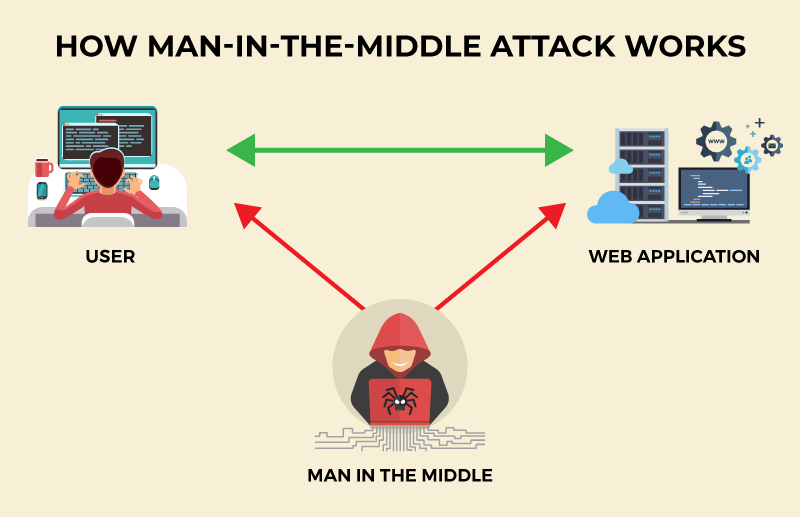
1. What is Man in the middle attack?
A Man-in-the-Middle (MITM) attack involves an attacker intercepting communication between a user and an application to steal personal information such as login credentials, account details, or credit card numbers for identity theft or unauthorized transactions.
2. How a MitM Attack Works
- Interception: The attacker positions themselves between the two parties. This can be achieved through methods like:
- Eavesdropping on unsecured networks: Public Wi-Fi networks are common targets.
- DNS spoofing: Redirecting traffic from a legitimate website to a fake one.
- IP spoofing: Pretending to be one of the communicating parties by altering IP packet headers.
- ARP spoofing: Associating the attacker’s MAC address with the IP address of a legitimate network device.
- Session hijacking: Taking over a session after the user has authenticated.
- Decryption: The attacker decrypts the intercepted messages if they are encrypted. This can involve exploiting weak encryption methods or using pre-installed malware.
- Relaying Messages: The attacker can pass on the messages between the two parties, making them believe they are communicating directly with each other. During this phase, the attacker can:
- Steal sensitive information: Such as login credentials, credit card numbers, and personal information.
- Alter the communication: Modify the data being exchanged, which can lead to actions like unauthorized fund transfers or incorrect information being sent.
In the first part, I will introduce you to ARP cache poisoning. This is a form of modern MitM (Man-in-the-Middle) attack with a long history (sometimes also known as ARP Poison Routing). This attack allows hackers to eavesdrop on all network traffic between the victim computers.
3. What is ARP Spoofing?
-
What is ARP?
ARP (Address Resolution Protocol) is a communication protocol used to map IP addresses to physical machine addresses (MAC addresses) on a local network. It allows devices on the same network to communicate by translating IP addresses into MAC addresses, facilitating the distribution of data packets between devices.
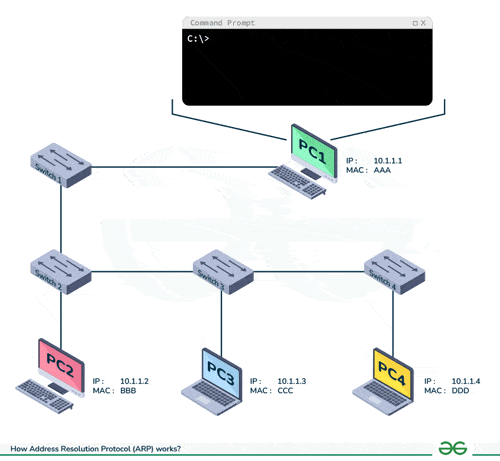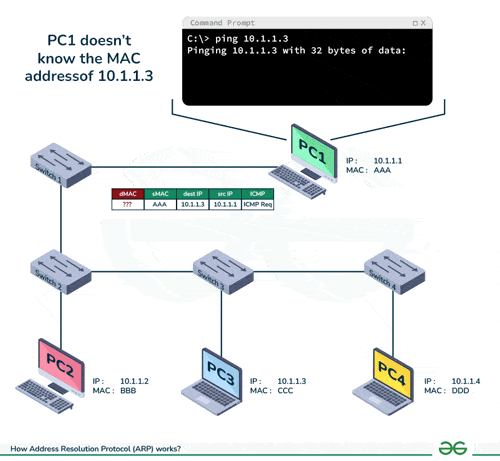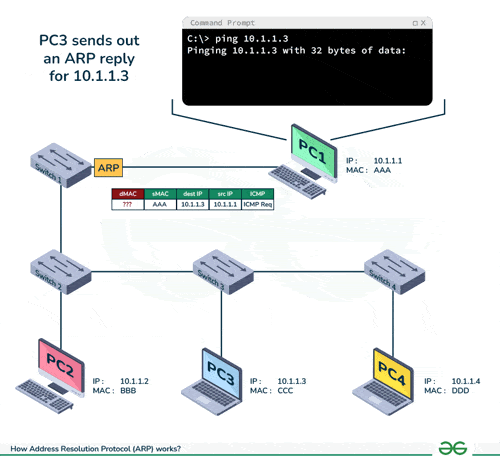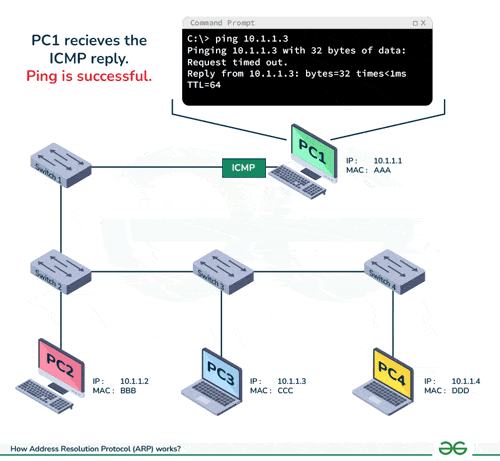
-
Why are both IP addresses and MAC addresses needed?
This is related to the operation of the Internet and, more specifically, the OSI model. This model defines how data is sent and received over a network. The OSI model consists of 7 layers, in which:
- Layer 2 uses MAC addresses and is responsible for distributing data from one hop to another.
- Layer 3 uses IP addresses and is responsible for end-to-end packet delivery.
When a computer sends data, it encapsulates the data within an IP header (which includes the source and destination IP addresses). This IP header, along with the data, is then encapsulated within a MAC header (which includes the source and destination MAC addresses).
As the data travels from one router to another, the MAC address header is removed and replaced with a new one. However, the IP header remains unchanged until the data reaches the final destination device.
Therefore, for the Internet to function properly, both MAC addresses and IP addresses are needed. MAC addresses facilitate data transmission at the physical layer, while IP addresses ensure that the data reaches the correct final destination device.
-
What is Spoofing?
- In a Man-in-the-Middle (MITM) attack, spoofing involves impersonating someone or something else. This can include impersonating a legitimate website, service, or user to intercept and manipulate data. Spoofing can involve IP address spoofing, ARP spoofing, DNS spoofing, or even SSL certificate spoofing. The goal is to deceive the victim into believing they are communicating with a legitimate entity while in reality, they are communicating with the attacker.
- And ARP spoofing is precisely the act of falsifying the ARP table (ARP cache) – a table containing information stored in the memory of computers, routers, or any other devices that use the ARP protocol.
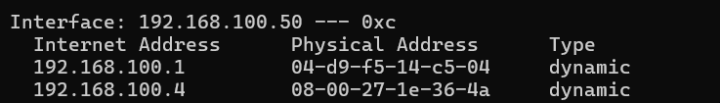
ARP cache
- ARP spoofing takes advantage of the inherent insecurity of the ARP protocol. Devices using the Address Resolution Protocol (ARP) will accept updates at any time. This means that any device can send an ARP reply packet to another computer, and the receiving computer will update its ARP cache with the new value. Sending an ARP reply when no request has been made is known as sending a “gratuitous” ARP. When these gratuitous ARP replies reach computers that sent a request, these computers will think that they have found the correct entity to communicate with. However, in reality, they are communicating with an attacker.
4. DEMO
Tool: Bettercap, BurpSuite
Attacker: Kali Linux
IP: 192.168.100.4
Victim: Windows
IP: 192.168.100.50
Bettercap interface:
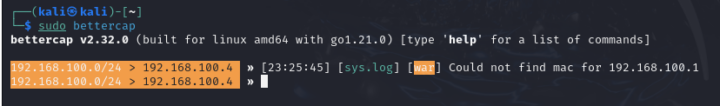
Tool: Bettercap
Now that we are using this tool, to attack Man-In-The-Middle, we must first identify which devices are connected to our network so we can impersonate and become Man-In-The-Middle. between. For this I will use the Bettercap net.probe module, we can find it by typing help on the Bettercap terminal.
To run net.probe we must type net.probe on. By this command, it will scan the devices connected to the network. To display the devices in table format, we will type the net.show command.
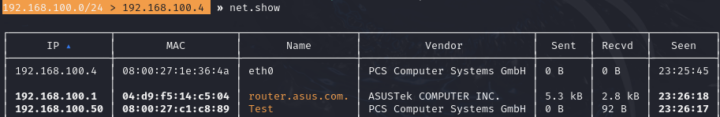
Display devices in table format using net.show
Secondly, we need to set arp.spoof.targets parameter by simply giving it the IP address of our victim. In my case set arp.spoof.targets 192.168.100.50
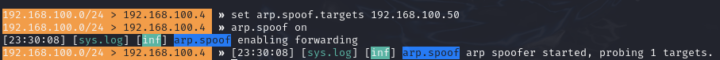
Now when we type arp.spoof on it will fire up the attack.

Before being attacked arp spoof
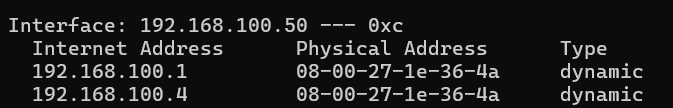
After being attacked arp spoof
You can see the arp cache has been changed and two different IPs are having the same MAC address
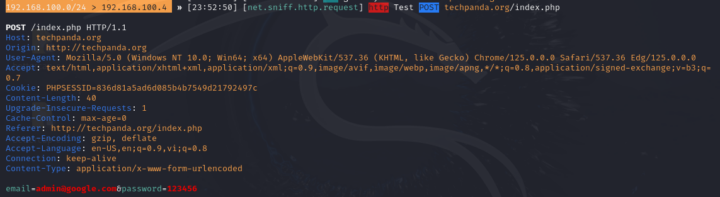
Now I am using two devices and to see the internet traffic I will use net.sniff module. So I just type net.sniff on and it will block all traffic.
And here are the results for websites using http:
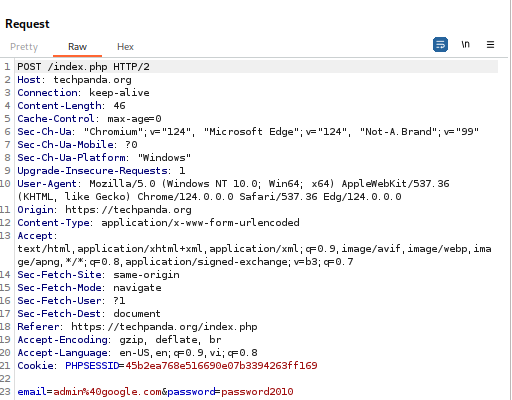
For https:
When connecting to the website, there will be an invalid SSL certificate warning.

SSL (Secure Sockets Layer) operates on the principle of encryption and authentication to secure communication between a client (such as a web browser) and a server. Here’s how it works:
- The client sends a request to access a secure page (URL starting with https://).
- The server responds by sending its certificate to the client.
- The client (web browser) verifies the validity of the certificate by checking the digital signature of the Certificate Authority (CA) accompanying the certificate. Assuming the certificate is validated and still valid, or the client intentionally proceeds even after being warned by the web browser that the certificate cannot be trusted (due to being a self-signed SSL certificate or expired certificate, or incorrect information in the certificate), then step 4 occurs.
- The client generates a random symmetric encryption key (or session key), then uses the public key (obtained from the certificate) to encrypt this session key and sends it back to the server.
- The server uses its private key (corresponding to the public key in the certificate) to decrypt the session key.
- Subsequently, both the server and the client use this session key to encrypt/decrypt messages during the communication session.
If you still accept an invalid SSL, your information can still be compromised. This emphasizes the importance of ensuring that SSL certificates are valid and trusted to maintain secure communication.
5. Ways to Prevent Man-in-the-Middle Attacks
To mitigate the risk of Man-in-the-Middle (MitM) attacks, implement the following preventative measures:
- Install antivirus software: Detect and block malicious activities.
- Avoid public WiFi access points, especially those not protected by a password: Reduce exposure to potential attackers.
- Log out when you’re done using a login-required site: Prevent unauthorized access through session hijacking.
- Use multi-factor authentication (MFA) whenever possible: Add an extra layer of security, making unauthorized access more difficult.
- Use websites that utilize HTTPS: Encrypt data transmitted between the user and the website, safeguarding it from interception.
- Use a Virtual Private Network (VPN) for sensitive transactions and communications: Encrypt internet traffic to maintain privacy and security against potential eavesdroppers.
Man-in-the-Middle attacks are a significant threat in cybersecurity, exploiting vulnerabilities in communication protocols and user behaviors. Understanding how these attacks work and implementing robust security measures can help mitigate the risks associated with them.


 EN
EN 日本語
日本語